Aufbauend auf unserem letzten Blogbeitrag über die Bedeutung und die Vorteile eines ISMS gehen wir nun näher auf die praktischen Aspekte seiner Umsetzung und die damit verbundenen Herausforderungen ein. Unabhängig davon, ob Sie ein IT-Fachmann, ein Experte für Cybersicherheit oder eine Führungskraft sind, erhalten Sie in diesem Beitrag wertvolle Einblicke in die besten Praktiken für eine erfolgreiche ISMS-Implementierung und in die Bewältigung gängiger Herausforderungen.

Beginnen Sie Ihre ISMS-Reise mit diesen Schritten
Der erste wichtige Schritt für eine erfolgreiche Einführung eines Informationssicherheitsmanagementsystems (ISMS) ist die Festlegung eines starken Projektauftrags. Dazu gehören die Definition des Anwendungsbereichs des ISMS, die Festlegung klarer Ziele und die Sicherstellung des Engagements der obersten Führungsebene. Das Projektmandat dient als Fahrplan, der das Unternehmen durch den gesamten Implementierungsprozess leitet. Lesen Sie in den folgenden Abschnitten mehr über die wichtigsten Schritte.

1. Erstellen Sie einen Überblick über Ihre Sicherheitslage
Generell ist es wichtig, ein grundlegendes Verständnis für Ihre derzeitige Sicherheitslage zu gewinnen. Dazu könnte beispielsweise die Wahl des Rahmens gehören, mit dem Sie arbeiten möchten, sowie eine grundlegende Bewertung der derzeitigen Umsetzung der Kontrollen. Prüfen Sie die Anforderungen und bewerten Sie in aller Kürze: "Tue ich bereits etwas für dieses Thema oder habe ich es noch gar nicht angefasst?". Auf diese Weise können Sie ein gutes Verständnis dafür bekommen, wie viel Sie tatsächlich noch tun müssen, um mit der Einführung Ihres ISMS voranzukommen.
Sobald Sie festgestellt haben , was Sie mit Ihrer derzeitigen Arbeit bereits abgedeckt haben, wird es einfacher sein, auch potenzielle Risiken zu ermitteln. Bitte beachten Sie, dass dies nicht unbedingt sofort als einer der ersten Schritte erfolgen muss. Es gibt viele Hilfsmittel, die Sie durch die einzelnen Schritte zur Erfüllung der Anforderungen leiten und bei denen die Risiken nicht von vornherein im Vordergrund stehen. Sie sind ein entscheidender Teil des Weges, Sie werden mit ihnen arbeiten müssen. Entscheiden Sie aktiv, wann und wie und suchen Sie nach dem richtigen Werkzeug, um Ihre Arbeit so effizient wie möglich zu gestalten.
Strukturierung Ihrer Arbeit und Aufteilung der Verantwortlichkeiten
Nach der grundlegenden Bewertung Ihrer derzeitigen Sicherheitslage bei der Evaluierung der allgemeinen Themenanforderungen eines Rahmens können Sie damit beginnen, die Verantwortlichkeiten mit Ihrem Team zu teilen. Wer ist für welches Thema verantwortlich? Wer hat Zugang zu den Informationen, die für die Anforderungen benötigt werden, und wer ist in der Lage, diese auch kontinuierlich zu überwachen? Es ist immer von Vorteil, wenn Sie ein ganzes Team und nicht nur eine einzelne verantwortliche Person zur Verfügung haben. So weiß ein Mitarbeiter der Personalabteilung vielleicht besser, welche Richtlinien beim Onboarding zu beachten sind, während sich jemand aus der IT-Abteilung besser mit der Implementierung einer Malware-Schutzsoftware auskennt. Sobald die Arbeit verteilt ist, kann jede Person mit ihren eigenen Aufgaben weiterarbeiten.
Risikobewertung
Wenn Sie sich für die Durchführung einer Risikobewertung entscheiden , konzentrieren Sie sich auf die Identifizierung potenzieller Bedrohungen und Schwachstellen, die Bewertung der potenziellen Auswirkungen und der Wahrscheinlichkeit dieser Risiken und die Festlegung geeigneter Kontrollen, um diese Risiken zu mindern.
Die Risikobewertung sollte umfassend sein und alle Bereiche der Organisation und alle Arten von Informationswerten abdecken. Sobald die Risikobewertung abgeschlossen ist, sollte die Organisation einen Risikobehandlungsplan entwickeln. Dieser Plan beschreibt die spezifischen Maßnahmen, die zur Bewältigung jedes festgestellten Risikos ergriffen werden sollen. Es ist wichtig, die Risiken nach ihrer potenziellen Auswirkung und Wahrscheinlichkeit zu priorisieren und die Ressourcen entsprechend zuzuweisen.
2. Einführung einer strengen Informationssicherheitspolitik
Ein weiterer wichtiger Schritt ist die Entwicklung und Umsetzung einer Informationssicherheitspolitik. Dabei handelt es sich um ein offizielles Dokument, das von der obersten Führungsebene der Organisation akzeptiert wird und in dem die Ziele der Organisation im Bereich der Informationssicherheit sowie die wichtigsten Maßnahmen zu deren Erreichung klar definiert sind.
Wenn sich die oberste Leitung verpflichtet, die Arbeit zu unterstützen und sich für die erreichten Ziele einzusetzen, steigt die Wahrscheinlichkeit, dass diese Ziele erreicht werden, erheblich. In der Informationssicherheitspolitik kommuniziert die oberste Leitung z.B. ihr Engagement für die Bereitstellung von Ressourcen, die kontinuierliche Verbesserung des ISMS und damit letztlich die Erreichung der gesetzten Ziele.
In der Informationssicherheitspolitik sollten auch die Aufgaben und Zuständigkeiten der anderen Mitarbeiter in Bezug auf die Informationssicherheit dargelegt werden.
3. Definieren Sie Ihr ISMS-Team
Der Aufbau eines erfolgreichen ISMS-Teams erfordert eine sorgfältige Auswahl von Personen mit unterschiedlichen Fähigkeiten und Kenntnissen. Das Team sollte idealerweise aus Mitgliedern verschiedener Abteilungen bestehen, darunter IT, Personalwesen, Recht und Betrieb, um einen ganzheitlichen Ansatz für die Informationssicherheit zu gewährleisten.
Das ISMS-Team sollte von einer hauptverantwortlichen Person geleitet werden, z. B. einem Chief Information Security Officer (CISO) oder einer vergleichbaren Funktion. Der CISO ist dafür verantwortlich, die Gesamtstrategie des ISMS zu überwachen, die Einhaltung der Normen, z. B. ISO 27001, zu gewährleisten und mit der obersten Leitung über die Leistung des Systems zu kommunizieren.
Ein ISMS-Manager oder -Koordinator ist eine weitere wichtige Funktion. Diese Person ist mit der täglichen Verwaltung des ISMS, der Koordinierung mit verschiedenen Abteilungen und der Gewährleistung der Umsetzung der ISMS-Richtlinien und -Verfahren betraut.
IT-Mitarbeiter spielen im ISMS-Team eine wichtige Rolle, da sie für die Umsetzung und Pflege der für die Informationssicherheit erforderlichen technischen Kontrollen verantwortlich sind. Sie sollten ein umfassendes Verständnis der IT-Infrastruktur des Unternehmens und der damit verbundenen potenziellen Sicherheitsrisiken haben.
Vor allem in größeren Organisationen sind auch Personal- und sogar Rechtsexperten wichtige Mitglieder des ISMS-Teams. Die Personalabteilung kann bei den Schulungs- und Sensibilisierungsprogrammen helfen, während Rechtsexperten sicherstellen können, dass die Informationssicherheitsrichtlinien des Unternehmens mit den einschlägigen Gesetzen und Vorschriften übereinstimmen.
Schließlich können Vertreter anderer Abteilungen einen wertvollen Beitrag dazu leisten, wie sich das ISMS auf ihre Tätigkeiten auswirkt, und dazu beitragen, dass das System wirksam in die Gesamtprozesse der Organisation integriert wird. Durch eine klare Definition dieser Rollen und Verantwortlichkeiten kann eine Organisation ein starkes ISMS-Team aufbauen, das in der Lage ist, beispielsweise die ISO 27001-Zertifizierung zu erreichen.
4. Top-Management verpflichten
Die Rolle der Führungskräfte bei der Bewältigung der Herausforderungen bei der ISMS-Einführung ist von entscheidender Bedeutung. Die Führungskräfte sind die treibende Kraft hinter der erfolgreichen Einführung eines ISMS. Sie geben den Ton für den Ansatz der Organisation in Bezug auf die Informationssicherheit an, indem sie die Bedeutung der Sicherheit und das Engagement der Organisation für sie festlegen.
Die Leitung ist für die Festlegung der strategischen Ausrichtung des ISMS verantwortlich. Sie legt den Umfang, die Ziele und die Richtlinien des ISMS fest und sorgt für die Abstimmung mit der Geschäftsstrategie der Organisation. Diese strategische Ausrichtung gibt einen klaren Weg für die ISMS-Implementierung vor und hilft, Herausforderungen in Bezug auf Umfang und Ausrichtung zu bewältigen.
Darüber hinaus spielt die Führung eine entscheidende Rolle bei der Zuweisung von Ressourcen für die Umsetzung des ISMS. Sie stellt sicher, dass angemessene Ressourcen, einschließlich Personal, Technologie und Budget, für die Umsetzung und Pflege des ISMS bereitgestellt werden. Dies hilft bei der Bewältigung von Herausforderungen im Zusammenhang mit Ressourcenbeschränkungen.
Und schließlich spielt die Führung eine entscheidende Rolle bei der kontinuierlichen Verbesserung des ISMS. Sie überprüft regelmäßig die Wirksamkeit des ISMS und treibt bei Bedarf Verbesserungen und Änderungen voran. Auf diese Weise wird sichergestellt, dass das ISMS wirksam und relevant bleibt und die Herausforderungen im Zusammenhang mit sich ändernden Geschäfts- und Sicherheitsumgebungen bewältigt werden können.
5. Sicherstellung der Sensibilisierung der Mitarbeiter
Auch Schulungs- und Sensibilisierungsprogramme sind für eine erfolgreiche Umsetzung des ISMS unerlässlich. Alle Mitarbeiter sollten über die Bedeutung der Informationssicherheit und ihre Rolle bei deren Aufrechterhaltung geschult werden. Regelmäßige Schulungen und die Weitergabe von Leitlinien für ein besseres Sicherheitsbewusstsein können dazu beitragen, eine Sicherheitskultur im Unternehmen zu schaffen.

Vier große Herausforderungen bei der ISMS-Implementierung
Die Vorteile eines ISMS sind zwar zahlreich, aber der Weg zu seiner erfolgreichen Umsetzung ist nicht immer einfach. Vom Verständnis des komplexen Rahmens von Normen wie der ISO 27001 bis hin zur Sicherstellung der Akzeptanz durch die Interessengruppen haben Unternehmen oft mit einer Vielzahl von Herausforderungen zu kämpfen.
Trotz der potenziellen Herausforderungen ist die Überwindung dieser Hindernisse nicht nur möglich, sondern auch eine lohnende Erfahrung, die die Sicherheit Ihrer Organisation erheblich verbessern kann. In den folgenden Abschnitten werden wir uns mit diesen Herausforderungen befassen und praktische Lösungen anbieten, die Ihnen helfen, ein ISMS in Ihrer Organisation erfolgreich einzuführen.
1. Umgang mit dem Widerstand der Mitarbeiter
Der Umgang mit dem Widerstand der Mitarbeiter während des ISMS-Einführungsprozesses ist eine häufige Herausforderung. Dieser Widerstand ist oft auf mangelndes Verständnis für das System, Angst vor Veränderungen oder Bedenken wegen der erhöhten Arbeitsbelastung zurückzuführen. Daher ist es wichtig, diese Probleme direkt anzugehen, um einen reibungslosen Übergang zu gewährleisten. Letzten Endes, geben mehr als 50 % der Unternehmen an, dass die Einführung eines ISMS ihre Cybersicherheit verbessert hat - Ihre Bemühungen werden sich also auszahlen.
Erstens ist es wichtig, die Mitarbeiter über die Vorteile des ISMS aufzuklären und darüber, wie es die allgemeine Sicherheitslage des Unternehmens verbessern kann. Dies kann durch Workshops, Leitlinien oder Informationsveranstaltungen geschehen. Ziel ist es, den Mitarbeitern den Wert des ISMS, seine Funktionsweise und die Auswirkungen auf ihre täglichen Aufgaben zu verdeutlichen.
Zweitens ist es wichtig, die Mitarbeiter in den Umsetzungsprozess einzubeziehen. Dies kann durch die Bildung funktionsübergreifender Teams erreicht werden, denen Vertreter aus verschiedenen Abteilungen angehören. Indem Sie die Mitarbeiter in den Entscheidungsprozess einbeziehen, tragen Sie dazu bei, dass sie sich stärker am Ergebnis beteiligt fühlen und Widerstände abbauen.
Eine weitere wirksame Strategie besteht darin, Bedenken über eine erhöhte Arbeitsbelastung auszuräumen. Dies kann geschehen, indem aufgezeigt wird, wie ISMS tatsächlich Prozesse rationalisieren und Aufgaben effizienter gestalten kann. Durch die Automatisierung bestimmter Prozesse können sich die Mitarbeiter zum Beispiel auf strategischere Aufgaben konzentrieren. Insbesondere ISMS-Tools können die Arbeit der Mitarbeiter sehr effizient machen und sogar ihre Arbeitsbelastung verringern.
Denken Sie daran, dass die Überwindung des Widerstands der Mitarbeiter keine einmalige Angelegenheit ist, sondern ein kontinuierlicher Prozess. Er erfordert Geduld, eine offene Kommunikation und das Engagement, eine Sicherheitskultur im Unternehmen zu fördern. Mit diesen Schritten können Sie dazu beitragen, eine erfolgreiche ISMS-Einführung zu gewährleisten.
2. Verwaltung begrenzter Ressourcen
Die Verwaltung begrenzter Ressourcen während der Einführung eines ISMS ist eine kritische Aufgabe, die eine strategische Planung und eine effiziente Ressourcenzuweisung erfordert. Sie erfordert ein sorgfältiges Gleichgewicht zwischen den verfügbaren Ressourcen und den Anforderungen des ISMS-Implementierungsprozesses.
Zunächst einmal ist es wichtig zu verstehen, dass es sich bei den Ressourcen nicht nur um finanzielle, sondern auch um zeitliche, personelle und technische Ressourcen handelt. Eine erfolgreiche ISMS-Implementierung erfordert ein engagiertes Team mit einem klaren Verständnis der Informationssicherheitsziele des Unternehmens. Dieses Team sollte sich aus Mitgliedern verschiedener Abteilungen zusammensetzen, um einen umfassenden Ansatz zu gewährleisten.
Zeit
Die Einführung eines ISMS ist kein Prozess, der über Nacht abläuft. Es erfordert eine beträchtliche Menge an Zeit, um sicherzustellen, dass alle Elemente des ISMS korrekt umgesetzt werden. Daher ist es wichtig, einen realistischen Zeitplan zu erstellen, der die sorgfältige Ausführung jedes einzelnen Schritts im Implementierungsprozess ermöglicht.
Finanzielle Mittel
Die Einführung eines ISMS kann kostspielig sein, insbesondere für kleinere Organisationen. Es ist wichtig, ein detailliertes Budget zu erstellen, das alle Aspekte des Implementierungsprozesses abdeckt, von der anfänglichen Bewertung bis zur laufenden Pflege des ISMS.
Technologische Ressourcen
Die richtige Technologie kann den ISMS-Implementierungsprozess rationalisieren und ihn effizienter und effektiver machen. Dazu gehört u. a. Software für die Risikobewertung, die Verwaltung von Richtlinien und das Management von Zwischenfällen.
Überwindung von Ressourcenproblemen
Es gibt Strategien, die helfen können, begrenzte Ressourcen während der ISMS-Einführung zu verwalten. Die Nutzung vorhandener Ressourcen, z. B. aktueller Technologien oder von Personal mit entsprechenden Fähigkeiten, kann zur Kostensenkung beitragen. Außerdem kann eine Priorisierung der Aufgaben auf der Grundlage ihrer Auswirkungen auf die Informationssicherheit der Organisation dazu beitragen, dass die kritischsten Aspekte des ISMS zuerst angegangen werden. Es gibt z. B. einige Tools, die Ihnen automatisch die kritischen Aufgaben zuerst anzeigen, so dass Sie mit den Aufgaben und Teilen Ihres ISMS mit der höchsten Prioritätsstufe beginnen und nach und nach mit den weniger kritischen Aspekten fortfahren können (siehe Beispielbild unten: "Priorität: kritisch").

Schließlich kann eine kontinuierliche Überwachung und Bewertung des ISMS-Implementierungsprozesses dazu beitragen, etwaige Ineffizienzen oder verbesserungswürdige Bereiche zu ermitteln. Dies kann die Organisation in die Lage versetzen, notwendige Anpassungen vorzunehmen und die Nutzung der Ressourcen zu optimieren.
3. Mit den sich entwickelnden Bedrohungen Schritt halten
Ein entscheidender Aspekt bei der Einführung eines ISMS ist es, mit den sich entwickelnden Bedrohungen Schritt zu halten. In der dynamischen Welt der Informationssicherheit ändern sich die Bedrohungen ständig und entwickeln sich weiter, so dass es für Unternehmen unerlässlich ist, der Zeit immer einen Schritt voraus zu sein. Dazu gehört die kontinuierliche Überwachung der Bedrohungslandschaft, das Erkennen neuer Schwachstellen und die entsprechende Aktualisierung der Sicherheitsmaßnahmen.
4. Das ISMS auf dem neuesten Stand halten
Eine regelmäßige Überprüfung des ISMS ist ein wesentlicher Bestandteil der Aufrechterhaltung und Verbesserung der Wirksamkeit der Sicherheitslage einer Organisation. Sie beinhaltet eine systematische Bewertung des ISMS, um sicherzustellen, dass es weiterhin den Anforderungen und Zielen der Organisation in Bezug auf die Informationssicherheit entspricht. Diese Überprüfung wird in der Regel in regelmäßigen Abständen, oft jährlich, durchgeführt, kann aber auch durch bedeutende Veränderungen im Geschäftsumfeld oder in der Sicherheitslandschaft ausgelöst werden.
Bei einer ISMS-Überprüfung werden verschiedene Aspekte des Systems untersucht. Dazu gehören der Umfang des ISMS, die Methoden der Risikobewertung und -behandlung, die Richtlinien und Verfahren sowie die Wirksamkeit der Kontrollen. Bei der Überprüfung wird auch beurteilt, ob die Organisation die einschlägigen Gesetze, Vorschriften und Normen, wie z. B. ISO 27001, einhält. Ziel ist es, alle Bereiche zu ermitteln, in denen das ISMS möglicherweise unzureichend ist oder in denen Verbesserungen vorgenommen werden können.
Eine ISMS-Überprüfung ist keine einmalige Aktivität, sondern Teil eines kontinuierlichen Verbesserungsprozesses. Sie sollte in die allgemeinen Governance- und Managementprozesse der Organisation integriert werden. Auf diese Weise wird sichergestellt, dass das ISMS wirksam bleibt und weiterhin das gewünschte Maß an Informationssicherheit bietet, wodurch die strategischen Ziele der Organisation unterstützt werden und die Zertifizierung nach ISO 27001 erreicht werden kann. Bei einigen Tools können Sie automatische Überprüfungszyklen einstellen, so dass Sie nicht den Überblick verlieren.

Kontinuierliche Überwachung durch Audits von Dritten, um den Erfolg des ISMS sicherzustellen
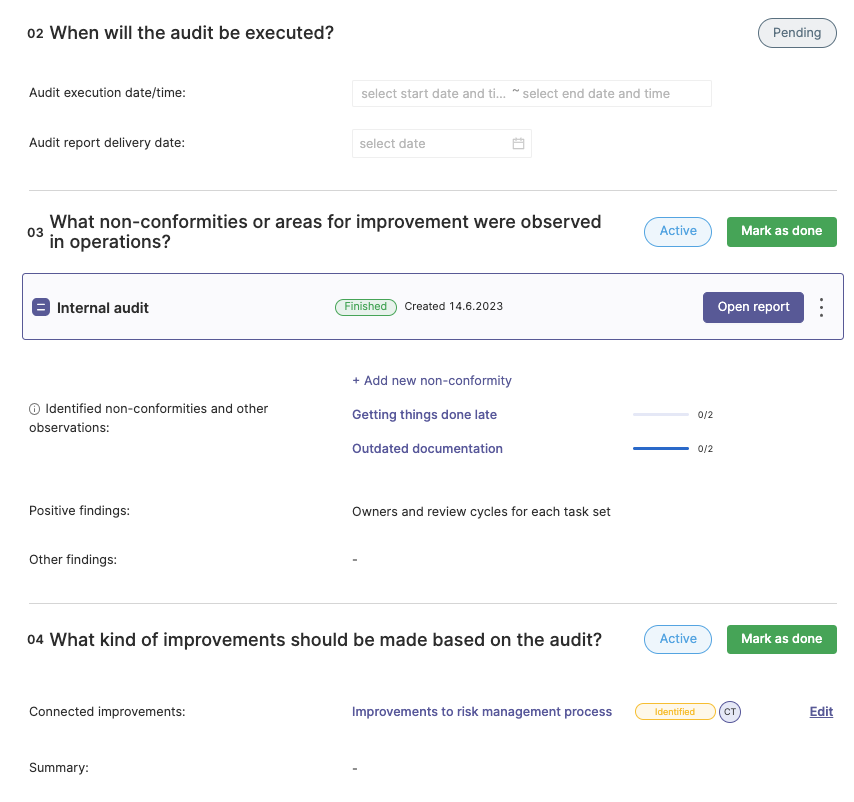
Sobald das ISMS eingerichtet ist, ist es wichtig, seine Leistung regelmäßig zu überwachen und zu überprüfen. Dies beinhaltet die Durchführung regelmäßiger Audits und Überprüfungen, um sicherzustellen, dass das ISMS wie vorgesehen funktioniert und alle Kontrollen wirksam sind. Alle festgestellten Probleme sollten umgehend angegangen werden, um eine kontinuierliche Verbesserung zu gewährleisten.
Auch bei internen Audits kann es für eine Organisation von Vorteil sein, ein Tool zu verwenden, anstatt alles von Grund auf selbst zu machen. Ein Audit-Tool kann beispielsweise eine zentrale Plattform für die Verwaltung aller auditbezogenen Aktivitäten bieten. Dazu gehören die Planung von Audits, die Zuweisung von Aufgaben, die Verfolgung des Fortschritts und die Dokumentation der Ergebnisse. Es kann auch die Kommunikation und Zusammenarbeit im Prüfungsteam erleichtern, was zu effektiveren Prüfungen führen kann.
Außerdem kann ein Audit-Tool zur kontinuierlichen Verbesserung beitragen. Es kann Einblicke in die Wirksamkeit des ISMS geben, verbesserungswürdige Bereiche aufzeigen und die Umsetzung von Korrekturmaßnahmen verfolgen. Dies kann Organisationen dabei helfen, ihr ISMS kontinuierlich zu verbessern und dadurch ihre Informationssicherheit zu erhöhen.
Weitere Einzelheiten über eine interne Auditfunktion in Aktion finden Sie in dem Cyberday über interne Audits.
Schlussfolgerung
Insgesamt erfordert eine erfolgreiche ISMS-Implementierung eine sorgfältige Planung, eine starke Führung und ein Engagement für kontinuierliche Verbesserungen. Indem sie diese Schritte befolgen, können Organisationen ihre Informationssicherheitsrisiken wirksam verwalten und beispielsweise die Zertifizierung nach ISO 27001 erreichen.
Das Erreichen der ISO 27001-Zertifizierung durch ein gut eingeführtes ISMS kann den Ruf einer Organisation verbessern und bei Interessengruppen, Kunden und Partnern Vertrauen in ihr Engagement für die Informationssicherheit schaffen. Sie kann auch einen Wettbewerbsvorteil auf dem Markt verschaffen, da sie zeigt, dass die Organisation die besten Praktiken im Bereich des Informationssicherheitsmanagements anwendet.
Daher können die Anstrengungen, die zur Bewältigung der Herausforderungen bei der ISMS-Implementierung unternommen werden, zu einer verbesserten Geschäftseffizienz führen. Durch die Identifizierung und Beseitigung überflüssiger Prozesse können Unternehmen ihre Abläufe rationalisieren und so Zeit und Ressourcen sparen. Langfristig überwiegen die Vorteile der Implementierung eines ISMS bei weitem die Herausforderungen, so dass sich die Investition für jede Organisation, die sich um die Informationssicherheit sorgt, lohnt.


.png)



























